Nmap
Scanning target is the easiest part
nmap ipaddresss
nmap -iL file_full_of_ipNmap will scan the first 1024 default ports so you will have to specify
-p : which port you decide to scan
-p- or -p 1-65535 : all portThere are many scanning methods:
-sS : stealth scan (send just SYN packets)
-sT : TCP Connect scan (send SYN and ACK packets, less stealthy since the etablishment of a connection will be present in the logs of the target host
-sU : UDP scan (send UDP packets, may be useful)
-sF/-sN/-sX : TCP FIN/NULL/Xmas the difference is the flag value in the header of the packets. Can sneak through some non-stateful firewallsYou can use the OS detection:
-OBut also the service detection:
-sVNmap comes with NSE scripts:
--script
--script-updatedb: to update the database
-sC : default NSE scripts
--script=http, banner, : you can combine multiple scriptsThe NSE scripts are on your local machine
For timing and performances:
--scan-delay <ms>: adjust delay between two packets send. It may be useful for to prevent IDS detection
-T <Paranoid 0|Sneaky 1|Polite 2|Normal 3|Aggressive 4|Insane 5> : from IDS evasion to speed scans (for fast networks for example)Finally the output format: You can combine nmap output with Metasploit. If you are using Metasploit, you can use db_nmap with
use auxiliary/scanner/portscan/... (syn/tcp/...)Otherwise you can export in XML format
-oX : XML output
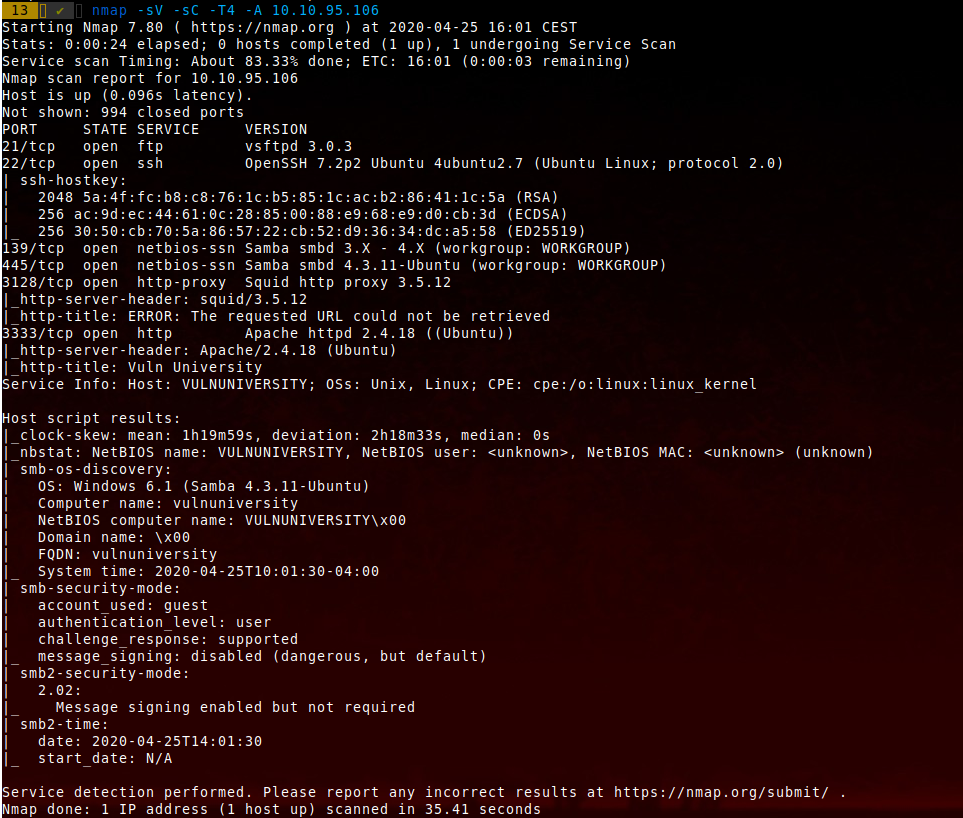
-oG : Gregable outputHere is an example